[Hashicorp Vault Hands On 2023] AWS Dynamic Secrets with Vault
https://play.instruqt.com/hashicorp/invite/eqpc1i6pthse
Instruqt
play.instruqt.com
Generate AWS credentials dynamically based on IAM policies.
Secrets engines are components which store, generate, or encrypt data. Secrets engines are incredibly flexible, so it is easiest to think about them in terms of their function. Secrets engines are provided some set of data, they take some action on that data, and they return a result.
Enable the AWS Secrets Engine
The AWS secrets engine generates AWS access credentials dynamically based on IAM policies. This generally makes working with AWS IAM easier, since it does not involve clicking around the AWS management console.
The AWS IAM credentials are time-bound and are automatically revoked when the Vault lease expires. The credentials can also be revoked at any time. You'll learn how to do that in a later challenge.
All secrets engines must be enabled before they can be used. Take a look at what secrets engines are currently enabled.
vault secrets list~ # vault secrets list
Path Type Accessor Description
---- ---- -------- -----------
cubbyhole/ cubbyhole cubbyhole_8aa67462 per-token private secret storage
identity/ identity identity_bdc48ee0 identity store
sys/ system system_ad683803 system endpoints used for control, policy and debuggingNote that the AWS secrets engine is not enabled. You should enable it.
vault secrets enable aws~ # vault secrets enable aws
Success! Enabled the aws secrets engine at: aws/By default, all AWS IAM credentials are paired with a lease of 768 hours, after which they will be revoked. You should shorten that to 30 minutes by updating the lease configuration located at the path /aws/config/lease.
vault write aws/config/lease lease=30m lease_max=30m~ # vault write aws/config/lease lease=30m lease_max=30m
Success! Data written to: aws/config/leaseAt any time during this track, you can view your root token by running:
cat /root/token~ # cat /root/token
s.yFmTBfwGHvW5gZ7ZrUxnUVPPThis token will be valid for the duration of the track. Typically, you'll set that token value as your VAULT_TOKEN environment variable with:
export VAULT_TOKEN=$(cat /root/token)~ # export VAULT_TOKEN=$(cat /root/token)If you open up the Vault UI tab and use this token, you can log into the UI and take a look around.
Configure the AWS Secrets Engine
Most secrets engines must be configured in advance before they can perform their functions. Vault supports three different types of credentials to retrieve from AWS.
This track focuses on the iam_user method, however, you can read more about the other options.
After enabling the AWS secrets engine, you must configure it to authenticate and communicate with AWS. You have been provided AWS credentials, so no need to use your own.
Since you enabled the AWS secrets engine on the default path, you can configure AWS by writing to the aws/config/root with a command that looks like the following:
vault write aws/config/root \
access_key=$AWS_ACCESS_KEY_ID \
secret_key=$AWS_SECRET_ACCESS_KEY \
region=us-west-1~ # vault write aws/config/root \
> access_key=$AWS_ACCESS_KEY_ID \
> secret_key=$AWS_SECRET_ACCESS_KEY \
> region=us-west-1
Success! Data written to: aws/config/rooFeel free to take a peek inside at the AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY environment variables.
echo $AWS_ACCESS_KEY_ID
echo $AWS_SECRET_ACCESS_KEY~ # echo $AWS_ACCESS_KEY_ID
AKIASQ44QO3CDLBBTNX6
~ # echo $AWS_SECRET_ACCESS_KEY
XmwCZRG5HDUZA8or0n2mAnliV9e8cAzfn41azDFQThe next step is to configure a role. A role in Vault is a human-friendly identifier to an action, that maps to a set of permissions in AWS as well as an AWS credential type. When users generate credentials, they are generated against this role.
Vault knows how to create an IAM user via the AWS API, but it does not know what permissions, groups, and policies you want to attach to that user. This is where roles come in - roles map your configuration options to those API calls.
In the example command below is an IAM policy that enables all actions on EC2. When Vault generates an access key, it will automatically attach this policy. The generated access key will have full access to EC2 (as dictated by this policy), but not IAM or other AWS services. If you are not familiar with AWS' IAM policies, that is okay - just use this one for now.
You need to map this policy document to a named role. To do that, write to aws/roles/my-role.
vault write aws/roles/my-role \
credential_type=iam_user \
policy_document=-<<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1426528957000",
"Effect": "Allow",
"Action": [
"ec2:*"
],
"Resource": [
"*"
]
}
]
}
EOF~ # vault write aws/roles/my-role \
> credential_type=iam_user \
> policy_document=-<<EOF
> {
> "Version": "2012-10-17",
> "Statement": [
> {
> "Sid": "Stmt1426528957000",
> "Effect": "Allow",
> "Action": [
> "ec2:*"
> ],
> "Resource": [
> "*"
> ]
> }
> ]
> }
> EOF
Success! Data written to: aws/roles/my-roleGenerate AWS Credentials
Dynamic secrets are generated when they are accessed. Dynamic secrets do not exist until they are read, so there is no risk of someone stealing them or another client using the same secrets.
In the last challenge you told Vault "when I ask for a credential for my-role, create it and attach the IAM policy { "Version": "2012..." }"".
Before you go any further, take a moment to list all of the users in your AWS account using the aws cli with:
aws iam list-users~ # aws iam list-users
{
"Users": [
{
"Path": "/",
"UserName": "v1h2eptj53j1c4md",
"UserId": "AIDASQ44QO3CE6MBLDKP4",
"Arn": "arn:aws:iam::173737539268:user/v1h2eptj53j1c4md",
"CreateDate": "2023-06-01T04:14:08Z"
}
]
}There should be only one user in the array that you receive back.
Now, with the AWS secrets engine enabled and configured with your role, you can ask Vault to generate an IAM access key pair for that role by reading from aws/creds/my-role.
vault read aws/creds/my-role~ # vault read aws/creds/my-role
Key Value
--- -----
lease_id aws/creds/my-role/zcCv02r3yMpEKa4ZDv16l6xA
lease_duration 30m
lease_renewable true
access_key AKIASQ44QO3CGIA4LYOK
secret_key 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
security_token <nil>Once you read from that endpoint, you will have generated new credentials and an associated lease.
That's not the only way to generate credentials, however. You can also do this through the Vault UI. Open up the Vault UI and log in with your root token. Remember that you can retrieve it using cat /root/token.

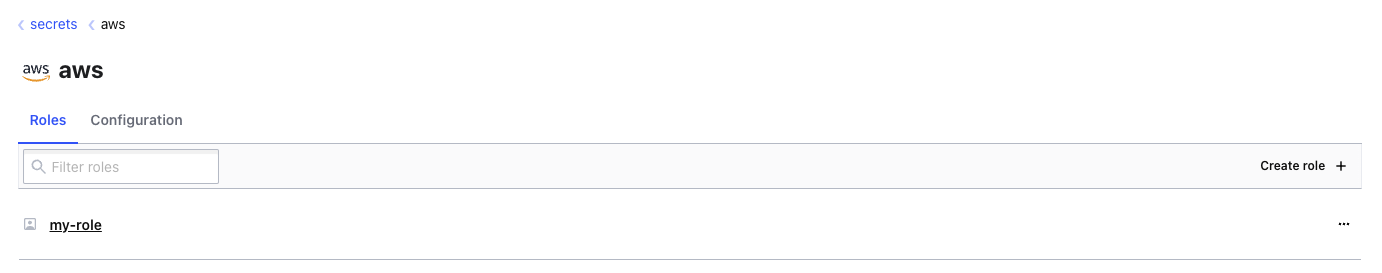
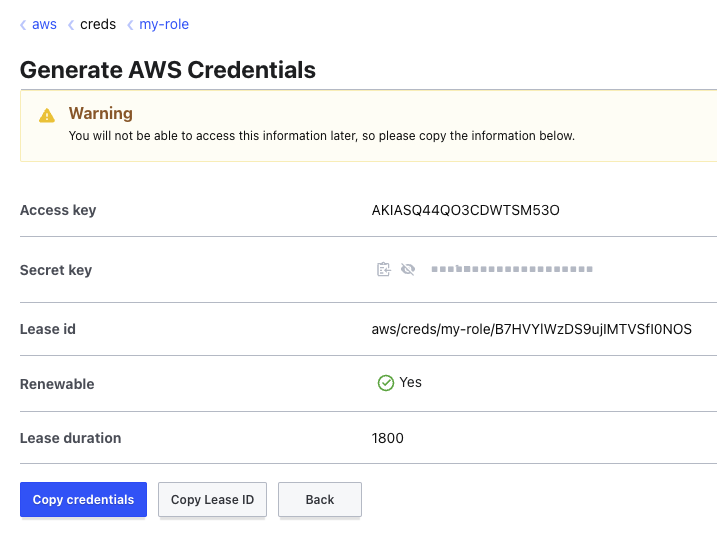
Once logged in, click on the "aws/" secret engine, then select "my-role". You want your "Credential type" to be "IAM User", then click "Generate". You'll see that just like you received on the CLI, you get an access key, a secret key and an associated lease.
If you list the users in your AWS account now, you should see the users you generated with a username prefix of vault-root-my-role-*:
aws iam list-users~ # aws iam list-users
{
"Users": [
{
"Path": "/",
"UserName": "v1h2eptj53j1c4md",
"UserId": "AIDASQ44QO3CE6MBLDKP4",
"Arn": "arn:aws:iam::173737539268:user/v1h2eptj53j1c4md",
"CreateDate": "2023-06-01T04:14:08Z"
},
{
"Path": "/",
"UserName": "vault-root-my-role-1685603040-55MYIQxGSFi5ipOzrSjt",
"UserId": "AIDASQ44QO3CDVS2B5ZOV",
"Arn": "arn:aws:iam::173737539268:user/vault-root-my-role-1685603040-55MYIQxGSFi5ipOzrSjt",
"CreateDate": "2023-06-01T07:04:00Z"
}
]
}You can also see all of the active leases for your role using:
vault list sys/leases/lookup/aws/creds/my-role~ # vault list sys/leases/lookup/aws/creds/my-role
Keys
----
zcCv02r3yMpEKa4ZDv16l6xA